Understanding Sender Policy Framework
Email authentication protocols are a first line of defense against potentially devastating email attacks. But what are email authentification protocols, and how can they be the gatekeepers of your digital mailroom, fighting the good fight against email fraud, spam, and phishing attacks?
Today we introduce a blog series that we hope demystifies the acronyms SPF, DKIM, and DMARC and explains how they work together to enhance email security.
Picture this: you’re a postman in the digital world, and you’ve got a letter to deliver. How do you ensure your letter ends up in the correct mailbox without getting intercepted? How do you prove you delivered a letter from the actual sender and not some scam artist trying to gain access to your recipient’s personal information? Enter SPF, DKIM, and DMARC, the triumvirate of email security. These three acronyms represent the essential email authentication protocols in use today: SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
This week’s blog focuses on the first of these protocols, Sender Policy Framework.
What is Sender Policy Framework?
Sender Policy Framework, or SPF, is an email authentication method designed to detect and block email spoofing. This is an all-too-common tactic used by malicious actors who send emails with a forged sender address to make it appear like the email is coming from a reputable organization or trusted contact.
SPF helps prevent spoofing by allowing receiving mail servers to check whether incoming mail from a domain comes from a host authorized by that domain’s administrators. SPF email records are similar to a public list that lets everyone know where you send your email from, and an email is treated as fake if it is not on that public list. In this way, SPF acts as a virtual doorman for incoming emails, checking if they originate from an approved server.
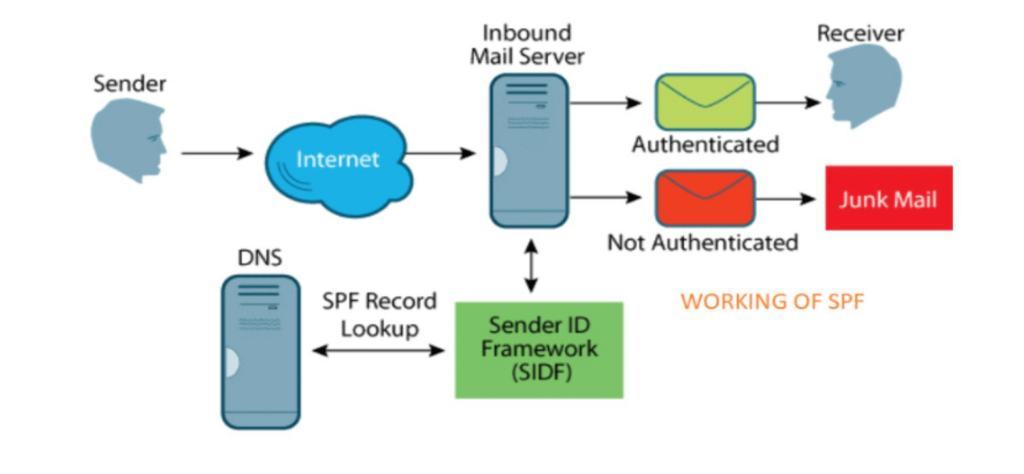
How does SPF work?
SPF is rooted in DNS (Domain Name System) records. A domain owner can create an SPF record that includes a list of all IP addresses authorized to send emails from the domain, and this record is then added to your domain’s DNS records.
When an email is sent, the receiving server checks the SPF record of the sending domain via DNS query. If the IP address of the sending server is found in the SPF record of the sending domain, the email passes the SPF check. If not, the email fails the SPF check and is typically marked as spam or rejected.
How is Sender Policy Framework beneficial to your business?
By using SPF as a first line of email defense, you can reduce email spoofing and phishing attacks. By validating the source of the email, SPF helps protect your brand’s email reputation, maintain the trust of your customers, and increase the deliverability of your emails. Without SPF, a domain becomes an easy target for spoofers. They can send emails that look like they’re from your domain, tricking your clients or partners into revealing sensitive information.
Final thoughts
While SPF is a powerful tool for protecting your domain against email spoofing, it’s not a standalone solution. It’s best used in conjunction with other email authentication protocols like DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance) for a more comprehensive email security strategy. We’ll cover DKIM in the next post of this series.
Get questions? Vernovis Consulting & Advisory can help!
Are you worried about your organization’s cybersecurity posture but unsure where to begin? Reach out today to talk to our team of cybersecurity experts who can perform an assessment or build a cybersecurity roadmap customized to your company’s needs. Let our team of experts help navigate your cybersecurity strategic challenges, giving you the confidence you need.






