Are you worried about the possibility of phishing scams and spoofed emails plaguing your organization’s inbox? If yes, it’s high time you wield the power of DMARC! This email security protocol is designed to shield your domain from email fraud and enhance deliverability. In our third blog in the series, we’ll demystify DMARC and highlight how it plays a crucial role in your email security strategy.
What is DMARC?
DMARC, or Domain-based Message Authentication, Reporting, and Conformance, is a policy framework that builds upon SPF and DKIM to provide comprehensive email authentication. It is a game-changer in the fight against phishing and email spam. At its core, it helps email receivers determine if a purported message aligns with who the sender claims to be. This robust technology hinges on a policy that instructs email clients on how to handle emails that fail DMARC checks.
How SPF, DKIM, and DMARC Work Together
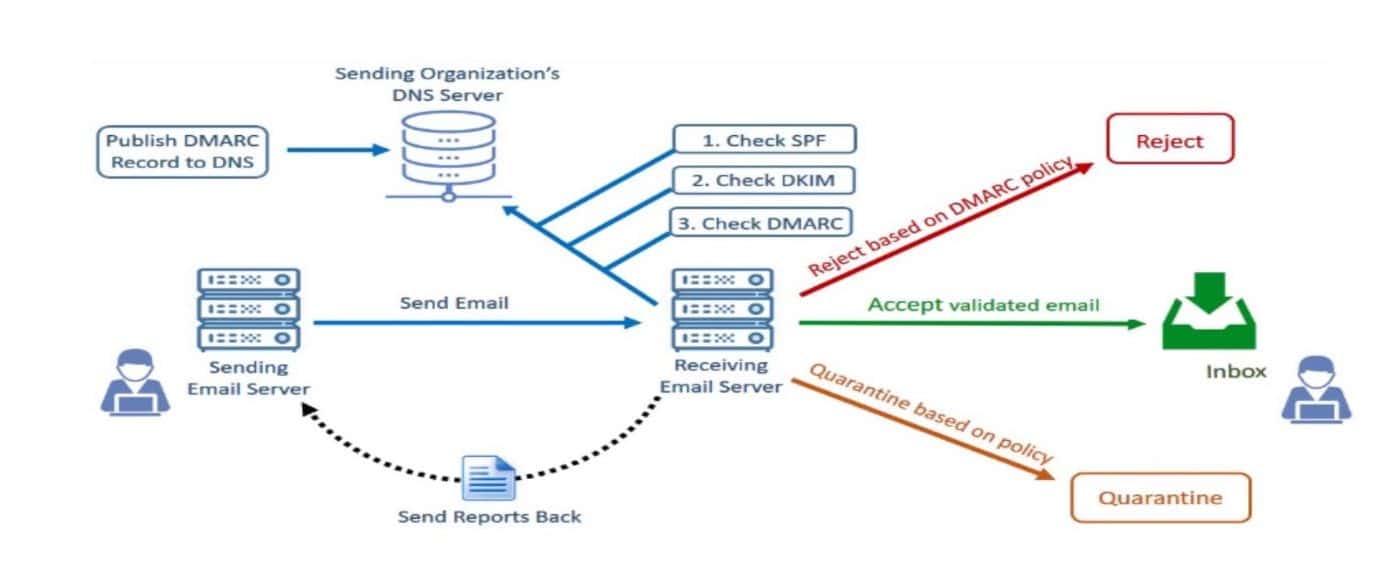
How does DMARC manage to combat email fraud so effectively? Let’s look at how it works with the other email security protocols we’ve discussed, SPF and DKIM, and the steps involved:
- Policy Declaration. As a domain owner, you publish a DMARC policy in your DNS records. You set the rules, defining what an email receiver should do when encountering an email that doesn’t meet the requirements. You can choose from ‘none’ (no specific action), ‘quarantine’ (treat as spam), or ‘reject’ (don’t deliver).
- Authentication. DMARC stands on the shoulders of two established technologies SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). SPF lets you, the domain owner, specify which mail servers can send emails on your behalf. DKIM, on the other hand, allows you to add a digital signature to the headers of your emails, which recipients can then validate.
- Alignment. Here’s the crux of it — for an email to pass the DMARC check, it must pass either SPF or DKIM authentication and be aligned. In simple terms, alignment means that the domain in the ‘From’ address should match the domain validated by SPF or DKIM.
- Verification. Upon receiving an email, the receiving server checks for a DMARC policy in the ‘From’ domain. If present, it validates the email against the SPF and DKIM criteria and checks for alignment.
- Reporting. Your DMARC policy specifies where to send aggregate and forensic reports. While aggregate reports give an overview of all received emails claiming to be from your domain, forensic reports offer insights on individual emails that fail DMARC checks.
- Action. Based on DMARC verification and the policy you’ve defined, the receiving mail server decides whether to deliver the email, flag it as spam, or reject it outright.
Why You Should Care About Email Security Protocols
Implementing DMARC is not just about preventing your domain from being used in phishing scams. It also enhances your email deliverability by reassuring email clients that your emails are trustworthy and legitimate. Furthermore, it boosts your domain’s reputation, increasing the likelihood that your emails land in the recipient’s inbox, not their spam folder.
In a world where phishing attacks are becoming increasingly sophisticated, email security protocols like DMARC are an essential line of defense. It is a policy framework that builds upon SPF and DKIM to provide comprehensive email authentication by helping domain owners set rules for how receiving mail servers should handle emails that fail SPF or DKIM checks. DMARC also enables domain owners to receive reports on email authentication failures, helping them monitor and refine their email security policies. By implementing DMARC, organizations can gain better visibility into their email ecosystem, identify and mitigate potential vulnerabilities, and protect their brand reputation from email-based attacks.
While no single tool can guarantee complete email security, SPF, DKIM, and DMARC can work in synergy to create a robust email authentication ecosystem, making your digital communications more secure.
Concerned about email security? We can help!
Companies are reporting phishing, whaling, and spoofing attacks are on the rise! If you are looking for experts who navigate the complex world of cyber, Vernovis can help! Learn more about our Consulting and Advisory Services, designed to help your technology infrastructure run efficiently and securely.






