Supply Chain Risk Proactive Defense and Zero Trust
 Catherine Bushong, Vernovis:
Catherine Bushong, Vernovis:
All right. On my side we’re right at the one o’clock. I know we still have some people joining. For those of you who are joining, please feel free to interact with us through the chat. We’re going to be polling some questions. We’ll start off and kick it off with some introductions. My name is Catherine Bushong. Most of you know me as Cat here in this region. I’m with Vernovis and we are a [00:00:29] shopping and solutions provider within technology and accounting and finance. We also have a separate cybersecurity solutions division. I sit on the board for our Women in Technology organization here in Cincinnati, and we’re also co-founding sponsors of ComSpark, so we get very involved in the community and when it comes to diversity and within technology in general. So, today I have the pleasure of talking with some amazing leaders within the cybersecurity space here in the area, and we’ll get ahead and make some introductions. Samara, if you want to kick us off. Tell us where you’re from, what your title is, what you did, and we’ll just go around the room.
 Samara Williams, Cardinal Health:
Samara Williams, Cardinal Health:
Hey, everybody. Samara Williams, Manager of Threat Operations at Cardinal Health. So, we’re out of Columbus, Ohio, but I’m originally [inaudible 00:01:18]. Our main focus as a threat operations team is threat intelligence and vulnerability management.
 Lisa Heckler, Caresource:
Lisa Heckler, Caresource:
Hi, I’m Lisa Heckler, I’m the Chief Information Security Officer for Caresource. Also, in addition to information security, I have privacy and business continuity.
Renee Tarun, Fortinet:
Hi, I’m Renee Tarun, I’m Deputy CISO at Fortinet. I focus on internal security, product security, and policy and complaints.
 Emily Morgan, Western & Southern Financial Group:
Emily Morgan, Western & Southern Financial Group:
Emily Morgan, I’m the Director of Cybersecurity at Western & Southern Financial Group, and I have responsibility for security operations, data protection, and cyber engineering.
 Oksana Shmaliy, Grange:
Oksana Shmaliy, Grange:
My name is Oksana Shmaliy, I am leading Identity and Access Management at Grange, and recently I also pick up functions of governance, risk and compliance.
Catherine Bushong, Vernovis:
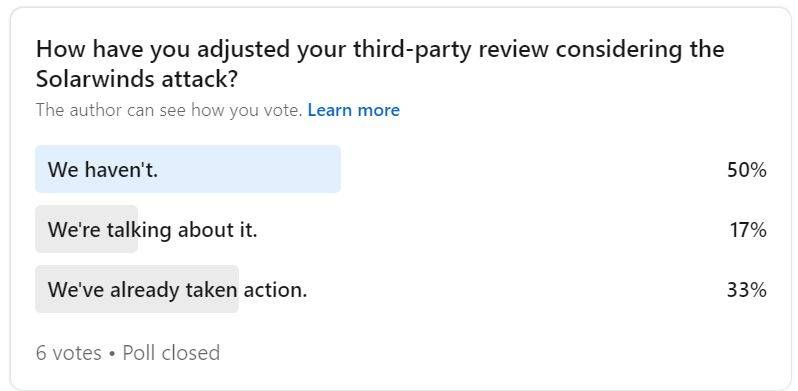
Okay, great. Thanks everyone for the introductions. So, for our panel, what we wanted to talk about, obviously kind of the SolarWinds attack might be old news for some people, but we wanted to revisit that topic to kind of focus on the style in which it occurred and the security around your supply chain, and how you’re managing your third-party risk associated with that. So, before we actually had this event we did some polling and 50% of the participants said that they have not changed their third-party reviews in any way, 17% said that they’re currently in conversations with their leadership about making some changes, and only 33% have actually taken action to adjust their third-party reviews. So, our first question, and we’ll go around, will be
How are you currently managing your supply chain risk and have you adjusted your third-party reviews at all?
Emily Morgan, Western & Southern Financial Group:
So, we have very established processes around third-party risk, both from a security perspective as well as business risk. So, one of the things that we identified was a gap. Not a gap, but a lack of focus on risk that wasn’t related to data access but related to pervasive access, so a tool like SolarWinds doesn’t have access to data but it does have privileged access throughout your environment. So, one of the things that we did was we took a step back, looked at the SolarWinds-like technologies that are environment and started doing reviews on them, and from now on they will be included on our third-party reviews as well.
Lisa Heckler, Caresource:
So, I’ll just tag onto that. We take the similar take, the usual approach; analyzing the data, tiering your vendors, contract language, looking at Security Scorecard, questionnaires, et cetera. Kind of the usual approach. What this really had us focusing on was the SDLC risk in a way that we hadn’t really considered previously, more so for cloud vendors, less so for internal vendors in the enterprise. Your trusted vendors, as Emily had mentioned, that have pervasive access, and/or privileged access across the environment. So, with that we did a full audit of those vendors and brought them more fully into our reviews, from a third-party risk perspective. And I’ll talk more about what else we did later, but just with respect to third-party reviews, we are amping that up and putting more emphasis on the SDLC review.
Oksana Shmaliy, Grange:
I want to add also, I think at our company they all focused on vendor management and risk management as well as business continuity and disaster recovery elements as part of your engagement with vendor, gain more visibility and more rigor, and especially our initial assessments on security. We actually following a much more extensive list of your traditional security questionnaire and if you read a little bit more on SolarWinds program it was actually a quoting program. Vulnerability was in the code itself and they exploit… they want to do [inaudible 00:05:59] was exploited, so when I’m thinking about our vendor management I think it also needs to go another level deeper, really understand what is their security development practices our vendor’s using to prevent certain vulnerabilities that comes to us when we engage with them, because we’re using their software. So, there is a little bit more of rigor around how you get inside into their own practices and their own coding practices that eventually can still put you in jeopardy, right? Because you acquire their software.
Renee Tarun, Fortinet:
Yeah. I mean, I would agree. I mean, from our perspective, we’ve always done the rigorous reviews on our suppliers, ensure that they’re doing their due diligence as per the procurement contract process, but I think Cat as you said, a lot of folks are saying that they haven’t necessarily changed their process because I think there’s also a lot of discussion around the fact that, what is the security review that we do when we’re doing… or our vendor’s doing, actually caught this type of attack? Because again, you’re dealing with a sophisticated nation state actor that… with a nation state actor, it was… as long as they have one motive at a time, resources and motivation, they’re going to find a way to get in. But what that doesn’t mean is that you don’t do your due diligence, because most organizations you have some form of complaints or regulatory requirements that have to be met. And besides nation states, you have other criminals and criminal groups that are looking to try and exploit any weaknesses or vulnerabilities, and any of the technologies that you’re using in your environment. So, you still have to do your due diligence, but I agree; a lot of it involves re-construing your software development or process. Asking those vendors the questions, are you doing vulnerability scans? Are you doing good coding practices? Are you teaching your developers work good habits and not bad habits? And so forth.
Samara Williams, Cardinal Health:
Just to tack onto what Renee is saying; 100% agree when it comes to the sophistication of this attack. People like me and the people through intelligence, we all… As much as it was terrible to see, I mean, it is such a cool… I mean, it’s a cool attack; it’s pretty genius how they went about it as well, right? So, it’s like, how do you get in front of something like this? And like Renee was saying, it’s a tough one, because they’re going to be looking at any which way avenue they can exploit, so we dove into the partnership between threat operations, security operations and third-party risk, to make sure that we’re all sort of communicating risk in the same way as well.
Oksana Shmaliy, Grange:
Yeah. It’s good point. And I also, I mean if we think about truly, how do you prevent something like that? You may not prevent, but then it depends on how quickly you able to react or detect that attack has happened, and what is your actions in terms of reducing the damage, right? And I think Renee actually mentioned that this attack was aiming gaining a privilege access within your internal systems, right? So, the one of the things that it’s very important is to have a very robust privilege access management processes, and in this case if, for example, I know we’ve [inaudible 00:09:20] all of us struggle to build the very robust temp processes, but one of the aspect there is regular password change, right? For all your accounts that have that privilege access. And I think investing in something like that internally can actually help you to position or be prepared when attack is actually happen, to quickly isolate or reset your password, remove… so even if somebody gain access to your privilege account with the password, if you change it, it means you right there already scope that action to go further.
Catherine Bushong, Vernovis:
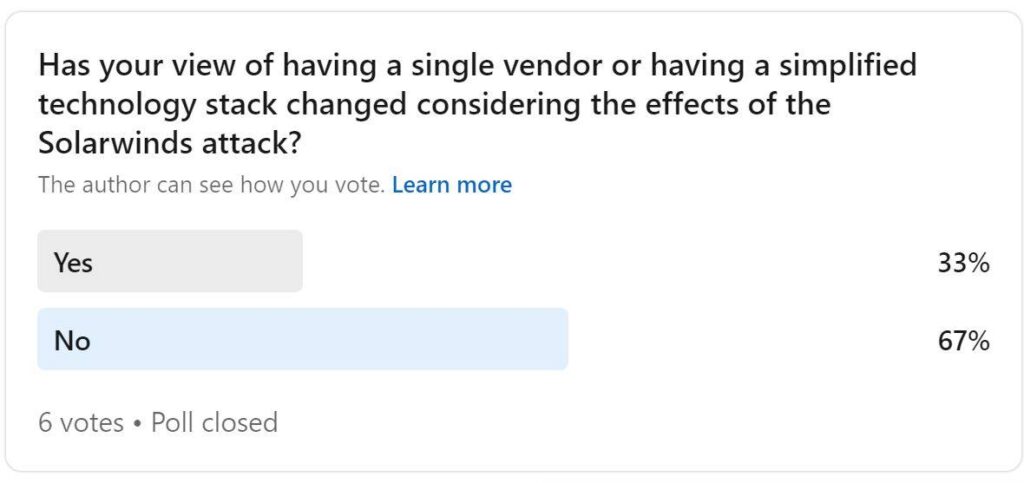
Sure. Well, good. When it comes to… I think we touched on it here in just a minute ago. I know Oksana and Renee had mentioned it also, but when it comes to your… the partners and vendors that you’re working with, most people are moving to having a simplified technology stack and having a one got-to vendor, and 67% of the participants that we polled said that this attack didn’t change their view of having that simplified stack. So, tell us a little bit more about how,
When you’re choosing your vendors whenever you’re working with them, what are the areas that you’re looking for gaps in their software or what are you going to look at first?
Renee Tarun, Fortinet:
Yeah. I mean, I know from my perspective, for me it’s making sure that the technologies that you select, integrate and work and play well within your environment. You can have the greatest, latest technology out there but if it can’t work with my current environment then it’s not going to be of value to me. Similarly, leveraging automation; cyber sex are now happening in a matter of minutes not seconds, and so you really need to be doing things at speed and scale, because our adversaries are doing things at speed and scale, and so being able to leverage technologies that take advantage of AI and machine learning to help automate in that environment, because again I think we all struggle with not having enough skilled resources and talents in our environments. And so again, for me it’s making sure that you have technology that will give you broad visibility across your entire environment, making sure that they integrate, work and play well with each other and technologies, and also [inaudible 00:11:47] of automation.
Lisa Heckler, Caresource:
I would tag on to that, Renee, and say additionally, I think it’s very important to increase monitoring. I think that that’s typically seen as lower risk, prior to the Solar Winds attack, and bumping up the risk profile and saying you’re UEBA and that you can’t sift through everything manually, so therefore having a good UEBA, that you’re leveraging and having appropriate level of risk associated with these kinds of vendors is helpful.
Oksana Shmaliy, Grange:
I mean, in terms of bringing in new technology in our business, in addition to when we’re using package software, I think one of the element when we use our custom development is to have a robust tools that does the vulnerability scanning, right? I mean, when we work with vendors we can probably ask and demand the result of their vulnerability scanning of their own software, and ask their procedures in place but then once we bring it in and if it used part of in your power processes or other applications, we have to have internal vulnerability scanning tools and processes working, and then not only just detecting them but have where follow-up procedures and a process that actually is going to address those vulnerabilities that we found within software, whether it is packaged software or our internal software we develop.
Catherine Bushong, Vernovis:
One of the questions that we had that just came through is, if vendors outline the difference between backup and disaster recovery, whatever you’re viewing your SLAs to recover from that attack, how are you viewing that, and how are you working with those vendors?
Oksana Shmaliy, Grange:
Can we listen like [crosstalk 00:13:47]-
Renee Tarun, Fortinet:
Could you repeat the question? I’m sorry, I didn’t see you on the chat.
Catherine Bushong, Vernovis:
Sure. [Eessa 00:13:52] had said that… I’ve put it in the chat right now. So, vendors outline the difference between backup and disaster recovery, so when you’re reviewing your SLAs, to recover from that attack what do you do?
Lisa Heckler, Caresource:
So, are you considering… is the question around how quickly you can restore from backup, or how quickly you… what your disaster recovery capability is in terms of recovery?
Catherine Bushong, Vernovis:
We’ll go back to Eessa-
Lisa Heckler, Caresource:
Are you talking about SLA with the vendor? Making them into contracts? Because certainly that’s what we would do from a disaster recovery perspective, and backups are a key part of that.
Renee Tarun, Fortinet:
Yeah. Backups that are tested and stored offline.
Lisa Heckler, Caresource:
Right. Key. Very Key.
Catherine Bushong, Vernovis:
Their key. Yeah. Yeah. And then you either [inaudible 00:14:43] of the timeline to recover and get back to work, so.
Lisa Heckler, Caresource:
Right. And I think your RTO, that’s very specific to your company, as well as the capabilities within your company.
Oksana Shmaliy, Grange:
I agree. It’s actually [inaudible 00:14:59] that is critical to that business application or critical to the business processes that application is involved. So, the whole recovery time is really has to be determined internally. There’s certain guidelines, but it is part of the… depending on what business process is and what is the place of that particular system, technology application, that part of the business process. I mean, there’s no kind of one answer to that, right? There is no specific “be back online in one hour” or, who knows? Maybe it is for the hour’s timeframe. It’s all depends on the business criticality.
Lisa Heckler, Caresource:
Exactly.
Renee Tarun, Fortinet:
Sure. And that’s going to vary by application as well. And perhaps by one business.
Catherine Bushong, Vernovis:
Yeah. And then we’ll touch on Leah’s question real quick.
For SMBs, should they look at partnering with experts?
Lisa Heckler, Caresource:
I think the answer to that is unequivocally, if I can say it, yes. Absolutely, to the degree that it makes sense for you financially, but talent is hard to find, bridging vendors, partners that can help you is key, especially for small and medium businesses.
Emily Morgan, Western & Southern Financial Group:
Yeah, especially in the monitoring space where that 24/7, 365… you are never going to be able to staff that as a small, medium business. It’s also the war on talent. It’s very difficult to staff with those experts, and they tend to be pretty niche, and in a small, medium business you need those generalists, so I would definitely purchase those niche and focus on keeping the internal what you need internal.
Renee Tarun, Fortinet:
Yeah. And I would add on to that, to what Emily said, I know it’s just that monitoring but I think also having those contracts in place when you need to do help with instant response. So, that may mean bring in someone to help you with doing forensics, or helping you to do mitigations. You don’t want to be wasting time going through your contracts and your precess and your legal or reviews and everything of contracts, because when things are hitting the proverbial fan, which they inevitably do, you want to be able to have those trusted partners a phone call away to say, “Yep. I need you and I need you now.”
Lisa Heckler, Caresource:
And Renee, that call out I think applies for any sized business. So, I think it’s a great point.
Catherine Bushong, Vernovis:
Okay. So, we’ll kind of move on to the second question also, and then get back to the questions in the chat as well.
But with the cybersecurity landscape constantly changing, what areas are you guys looking at individually that your organizations are focusing on to defend against emerging attacks?
Samara Williams, Cardinal Health:
Yeah. I’ll jump on this one. So, from my perspective from a threat intelligence and vulnerability management, I think your team and your… is only as strong as its collection, right? Internally, externally, understanding that the threat activity in the external trends taking place, as well as be able to match that up with what might be happening internally, and be able to prioritize vulnerability management as well based on that intelligence. So, that’s where we focus quite a bit is understanding what’s actually happening out there, what we’re seeing, and like Emily said, working with those niche partners with the dark web monitoring space and being able to effectively communicate that to other teams to partner and start to tackle some of that proactive defense.
Oksana Shmaliy, Grange:
I think that’s a big area and it’s for everyone, and we had a lot of good discussions there on data here. At the day conference, but it’s also about data protection, right? We see, et cetera, there is so much out on data, and especially because of the privacy law where consumers can opt out and get their data back, and we know the challenges there is that not all the companies understand where actually customer data is and how do they protect it. Does it protect it or not? And then do you have a mechanism really to allow people to opt out and get their data back, right? So, that’s probably one of the big challenges. In our area… just going to piggy back on what Samara said; vulnerability management. In our cases, we kind of try to tie the vulnerability management with risk management, because if you don’t address your vulnerabilities it becomes your risk. So then all our risk-related procedures needs to be centered around, are we maintaining the best security posture in addressing non-vulnerabilities, and are we ahead of the vulnerability curve? Meaning if any new vulnerability comes, how quickly we can react and figured it out; where is it within our system and who needs to really take an action? So, those are other things on my mind, for example, right now.
Renee Tarun, Fortinet:
Yeah. I mean, I think-
Lisa Heckler, Caresource:
Go ahead, Renee.
Renee Tarun, Fortinet:
Yeah. So, I think from my perspective it’s really also looking at that zero trust access. Traditional security models operate on the assumption that everything can sign your organization and sign your network should be trusted. However, automatically extending trust to any device or user, you really put your organization at risk, whether it becomes compromised intentionally or unintentionally. So, from my perspective it’s a lot of organizations are churning to zero-trust model, because it kind of shuts that fundamental paradigm from open networks that are built around inherent trust, to a zero-trust framework through the adoption of reduced network access control. Because at the end of the day, if there are intrusions you really kind of need to know who and what is accessing your networks. And so, understanding who is users… we talked a little bit about that privileged management, but also understanding that you’re using things like multi-factor authentication and any additional layers beyond traditional users love passwords, because we know that’s where our adversaries are targeting, especially with the social engineering and phishing attacks. But also making sure you’ve got those headless devices, like IoT devices and BYOD devices coming into your environment. So again, shoring up those avenues where, again, I was at risk and levered to get into your network.
Lisa Heckler, Caresource:
So, you stole my thunder, Renee. Those were two things I wanted to touch on, especially MFA; no, it’s awesome. You said it very well, I’m sure better than I could. The only thing I would add to that specifically is the thing… all of that is awesome, and it makes really good sense from a [inaudible 00:22:11] especially MFA, but I would add to that just the basic security hygiene; cyber hygiene. It’s a slog. It’s not something that anyone really wants to put their time and energy into, but it’s a basic blocking and tackling that can really make a big difference. And in the DIW management, access management, doing the hard work to get to zero trust because you really have to know what people need access to, what roles need access to what, and really rationing down what that access looks like, instead of the operational easy path of just “have everything” kind of thing. It can make a big difference in your entire landscape as well as your ability to respond to an attack..
Oksana Shmaliy, Grange:
I want to get to the zero trust. I mean, today we trust our partners and we give them access very easily and quite quickly to all our system, right? But I think that one of the things… and I’m kind of come from the perspective of identity and access management, it’s very important, it’s critical to actually manage that access that we’re giving to our external partners. And today, for example, I mean, we still rely on Active Directory, Microsoft services, but in many cases I think that one of the things to protect your system is maybe use another… a different identity access… identity provider system like Okta to actually manage your external users and not allow really direct access to your internal systems. So, that’s one of the aspect, and I think it’s also course aligned with your zero trust, and when you input anybody into your system I think the best things you can do is really think about what is your list access you need to give them, right? How do you protect yourself, from giving them only minimum access needed, and then have a very good mechanism and automated ways to remove that access immediately if contract expires or when user becomes inactive, because honestly, looking at… knowing the inside data, we know that sometimes we don’t pay enough attention of all the consultants we bring on board that we give access.
Oksana Shmaliy, Grange:
And if we don’t have those keener processes where removing access, we are leaving a lot of loopholes within our system to be exploited down the road. So, that’s I think another aspect to consider; protecting our relationship with vendors.
Catherine Bushong, Vernovis:
Well, so the next question that we have is,
After the SolarWinds incident occurred, there was a lot of best practice recommendations that came out, so let’s talk about how you’re following up on those, and how you’re prioritizing those best practices through different things, such as with privilege access management or within your Microsoft 365 environments?
Emily Morgan, Western & Southern Financial Group:
So, for us we have a very good risk management process and risk management program, and so there were certain things that we took action on immediately because they were very critical to do so. The rest of the recommendations were really putting into that risk register and that risk prioritization process because what you can fall into is another risk, which is the urgency of something being right here, right in front of you, and sometimes there’s something over here that was identified previously that’s a higher risk but you’re not necessarily looking at that because you’ve got this urgent thing in front of you. So, we are very careful to, “Okay, let’s take a step back with these things that aren’t as urgent and make sure that they are prioritized appropriately.” So, we were undertaking an audit of the environment, so ensuring that what we think is true is true, in terms of verification of log-in and alerting capabilities around our trusted vendors, as well as reviewing our outbound internet access from our servers, so making sure that that attack surface is as small as possible. You can’t get out to the internet to go places that will [00:28:00] additional malware or [00:28:02] on the server then you’ll reduce risk.
Renee Tarun, Fortinet:
Yeah. I mean, from my perspective, and we weren’t infected by SolarWinds but I can talk, too, about… from the perspective of talking to a lot of our customers. Surprising, a lot of our customer when they came to us didn’t even know they were running SolarWinds in their environments, and so that goes back to having that asset management, and all it just means devices, knowing what all the software you’re running in your organization. And then also, taking steps to ensure you’ve got the proper end-point protection; again, end-points are often the first point of compromise, and so making sure that you’ve got the solutions in place to protect your end-points for their next end-point protection with the anti-virus, anti-malware but also having that EDR solution, end-point detection and response.
Oksana Shmaliy, Grange:
Well, I can add a little bit on the privilege access. I think because part is in your whole attack is the gaining access and ability to utilize those privilege access. I think that most important for any organization is understand what is the footprint of your application, especially if application use service accounts, number one, because you can exploit those service accounts password and [picturalizing 00:29:16]them you can… because those service accounts usually granted a lot of permissions within your systems, right? So, number one, having a very robust system in place, something like Password Vault where the whole application development and architecture needs to be centered around that Password Vault. So, all the application when they need access to run certain processes is actually reaching out to the Password Vault to check out that service account was password, so it’s not known to human beings, right? So, kind of isolating that footprint where the service accounts is exposed, they need to be really under that Vault, and only few people or few processes gain access, and that one thing.
Oksana Shmaliy, Grange:
And the other one we talked about actually, [inaudible 00:30:03] privilege access accounts, is that again, there are a lot of solutions where you have to enable people to use through the particular system to gain access to your servers and do administrative work. And so, in order to do that… actually, when you go through that particular system, like example would be BeyondTrust, password safe in BeyondTrust privilege access management capabilities, the BeyondTrust will at least record what was happening on the server and who was the actual person that did any of the changes in your system. So, having these capabilities within your organization can enable you to really have a better grasp of all your ban activities, and you can build a much better, more preventive as well as more detective controls within your organization.
Renee Tarun, Fortinet:
Yeah. The only thing I’ll add to that is that when we start looking at these best practices or recommendations and move towards remediating a lot of these gaps, having… and depending upon the size of your organization, but having your red team or your purple team validate those remediations, that’s key.
Catherine Bushong, Vernovis:
All right. So,
When we talk about your vulnerabilities and exposures, how are you relaying that in similar incidents that occur, where your gaps are in your screening process? How are you relaying that to your leadership teams?
Renee Tarun, Fortinet:
I mean, from my perspective, it really comes down to when you’re communicating the risk to the leadership team. From my perspective, when you’re talking to the leadership or even your board, it comes down to how you communi… [inaudible 00:31:51], save that for your technical team. You’ve got to communicate these risks into the context of… I’m assuming that for most organizations, senior leaders are focused on, how can we be more productive? How can we increase our revenue? How can we be more efficient? So again, put in the context of some of these kind of risks that we face in the cyber space, what they mean to the business. And also kind of signal the critical risks. Sometimes people get lost in the weeds by focusing on lower priorities versus focusing on the most critical cyber risks to the organization.
Renee Tarun, Fortinet:
And last but not least, making sure the cyber risks is a team sport across the organization. A lot of times people think that, “Oh, the cyber risk is the IT and security teams’ problems.” Well, yes, but at the end of the day the business owners have a role in that, and they should understand that business risk is, at the end of the day, sometimes we can make a recommendation and not to go with a specific third-party product because we think there’s vulnerabilities or concerns with it, and at the end of the day sometimes the security and IT teams can get overwritten by the executive team, and that’s okay but those risks got to be documented in a risk register and also documented who accepted those risks. And so, making sure that you identify those risks but also know who accepts that risk.
Lisa Heckler, Caresource:
So, I would add to that, Renee… you’re spot on, on across the board with the points that you made. But the time to communicate a risk to an executive you obviously, you need to be timely with that, but you need to have that relationship ahead of time. So, really making sure that you’re building trust and building your relationships and communicating risk in a way that resonates with your business partner, all the way across the board in a continuous way so that you have a partner across the table, and when the dom kids [inaudible 00:34:00] you want that partner to look at you and trust what you’re saying to them, because you’ve built that confidence of trust over time and you’re not just coming with, “Oh, and now the sky is falling, and we need to do X, Y, Z, and we’re in this really uncomfortable place.”
Lisa Heckler, Caresource:
So, I would just say, every day you should be working on how you communicate risk, and building the relationships and really understanding your business partner’s perspective, what’s important to them, and how to communicate with them in a way that resonates.
Emily Morgan, Western & Southern Financial Group:
That is exactly what I was going to say, and I completely agree with everything that’s been said. Also, in that communication, what is the avenue that that executive or that business partner wants to be communicated with? Because there are some people that you have to pick up the phone and talk to. Others want a very concise email. Others want a formal report, and so understanding that before the things get critical is very key. But then having those regular touch bases, whether it’s a steering committee or some other type of… just a… you’ve got those risks in front of them all the time, so it’s not a surprise when it’s like, “Oh, we’re asking for more money.” They’re very familiar with, what are the risks? And when you get to the point where it’s like, “Okay, this is what we need to do to address these risks,” they’re already going to be on board. And so, that’s where those relationship sand that trust really comes in.
Oksana Shmaliy, Grange:
I just want to add, I think sometimes you can use forma mechanism to kind of establish a relationship, but also through the host mechanism you build transparency. For example, we have a quite a good structure and our risk management there is internal technology-related risk meetings, and what we do, we invite our partners. We invite our auditors, but we also invite our enterprise risk management team, so we reach that transparency. So, whatever problems or challenges we’re facing, they are known to others. That’s kind of one of the ways to go about it. And then we have these formal [inaudible 00:36:30] meetings where again all our partners, not just the technology organization but business representative, and again our chief compliance officer and our risk management team is present. So, we work together. I mean, I agree with Lisa; this is really the way to kind of build a partnership, but being transparent and really discussing together all those known risk and understanding how their organization… what organization needs to do to address them.
Samara Williams, Cardinal Health:
Yeah. I don’t want to be the only one who doesn’t speak up here, but it’s a challenge that we experience on our team every day, Making sure that we’re not crying wolf and we keep the risk rating as objective as possible. But then also making sure that our technical risk evaluation folds right into the business risk as well. So, I know I’m regurgitating what you guys said but, you know?
Lisa Heckler, Caresource:
But it’s a great point, Samara, in terms of how you communicate risk. If you’re always saying, “The sky is falling,” then everything’s on fire and you lose your voice and you lose your impact in terms of when something really is on fire. So, I think it’s a point worth reiterating.
Catherine Bushong, Vernovis:
Sure. Okay. Well, and then we’ll kind of go back with that one more question to touch on. So, wanting to know everyone’s thoughts on data encryption and proactive defense, such as with data encryption at rest. So, if anybody wants to touch on this last question that we have from the viewers.
Lisa Heckler, Caresource:
Well, being in the healthcare space, that’s unequivocally a requirement, so yes.
Oksana Shmaliy, Grange:
And same here, it is yes. Yes. We had a formal program couple of years ago where we actual look at all our systems and we did a lot of work around data at rest encryption as well as data in transition encryptions mechanisms. So, yes, yes, and yes.
Catherine Bushong, Vernovis:
Well, good. Well, that’s all the questions that we have. I know we still have about five minutes to wrap up. Anyone, if you have any questions, please feel free to throw it in the chat now so we can get with them. As we’re kind of wrapping things up, let’s talk about…
As we’re moving forward, what are you looking at within your organizations, and what is it that you’re focusing on with the rest of this year?
Oksana Shmaliy, Grange:
Can I start? One of the things that I also do, and I always joke, it’s kind of like a hobby but it just still was in our organization; I’m leading security development and life cycle practice as well, and what I see through that practice is that if we want to impact security or really build organization that cares about security, we have to invest in building that culture, which really means changing behavior and helping people to think about security as part of their daily work. And I know that, sometimes the changed behavior, it’s not about just giving information to people but really finding your way where they can act, which mean they change something the way they do daily tasks. For example, we talk about that software, vulnerabilities which… it really depends on the developer that specific activities like unit testing or code reviews, or running scanning, study code analysis scanning or whatever any other practices, and that’s the only way with that building that culture, is impacting our daily actions. So, that’s kind of fixing on my mind.
Samara Williams, Cardinal Health:
Yeah. One thing we’re focusing on, because “never let a good crisis go to waste”, right? Is threat modeling, and thinking like the hackers, because like Renee was saying earlier, very sophisticated, your actor, and they’re going to continue to think outside the box and use the tools at their disposal, so we need to do the same.
Oksana Shmaliy, Grange:
Thank you for mentioning threat modeling. This is one activity we took on last year, and it is a huge, huge change, and I can see from inside how much… I wouldn’t say struggle, but it just a different mindset to approach something before you and building it, thinking about where the potential problems can be. What is it attacks? What is the exploits of that attacks that we can create ourselves, right? So, I mean, it’s a huge deal. For us it’s the same thing. Threat modeling is one of part of the programs that I mention.
Emily Morgan, Western & Southern Financial Group:
So, one of the things that we started down the sojourney several years ago, and we’re still continuing on that because there are too many things to look at and there are too many disparate systems and things like that, so trying to really get our reading in one place, and then ultimately… well, basically automating the stupid stuff. The stuff that I don’t need my humans to go look at; I need them to take that information, synthesize it and com out with a outcome. I don’t need them to go, “I need to go this, I need to go…” I don’t need that. So, that’s why… and we’re also automating vulnerabilities as well, because that’s another one that… gathering that information is so difficult, I just need people to be able to take it and do it. So, that’s another big thing we’re still continuing.
Renee Tarun, Fortinet:
Yeah. I would definitely agree with Emily. We’re merging our sort of technology to again automate some of those mundane tasks, as well as focusing on doing more on the security awareness training. Again, it comes at the end of the day, you are seeing more sophistication and some of those social engineering attacks, the phishing. Right now, we’re not even seeing the malicious links or attachments, so there’s no technology that’s going to stop that. I mean, we’re seeing the types of attacks that are focusing on just changing the banking routing information because we’ve had a supplier or a vendor if their emails been compromised, so again, it’s making sure that our employees have that security awareness to understand that something doesn’t seem right, it’s probably not. To take that second look and second guess things before acting.
Catherine Bushong, Vernovis:
Yep. Okay. Well, now we’ve got about one minute left. I just wanted to take a second just to thank all of our panel members for taking the time to come and speak and provide some insight into the public. Another thing to know; aside from all of the little events that we have going on sporadically, for ComSpark specifically make sure that your marking your calendars because we do have the ComSpark Cybersecurity Summit coming up later on this year on July 28th, so please make sure you mark that down, and thanks again everyone for your time and for joining us.







